Your CEO is on the line; But its not them
𝗬𝗼𝘂𝗿 𝗖𝗘𝗢 𝗜𝘀 𝗼𝗻 𝘁𝗵𝗲 𝗟𝗶𝗻𝗲; 𝗕𝘂𝘁 𝗜𝘁’𝘀 𝗡𝗼𝘁 𝗧𝗵𝗲𝗺 !
Imagine authorizing a wire transfer while looking your CEO in the eye… and being wrong. 🎭🤖
📝 Phishing isn’t about typos anymore. It’s 𝗱𝗲𝗲𝗽𝗳𝗮𝗸𝗲𝘀, 𝗰𝗹𝗼𝗻𝗲𝗱 𝘃𝗼𝗶𝗰𝗲𝘀, flawless emails and 𝗵𝘆𝗽𝗲𝗿-𝗽𝗲𝗿𝘀𝗼𝗻𝗮𝗹𝗶𝘇𝗲𝗱 𝗹𝘂𝗿𝗲𝘀 that are written just for you.
🔎 Case in point:
❌ In Hong Kong, a finance clerk wired $𝟮𝟱𝗠 after joining a fake video call with deepfake versions of their CFO and senior execs. ❌ In Germany, a CEO’s voice was cloned from a 30-second clip, leading to a fraudulent $243K transfer.
🚨 AI as a Force Multiplier for Cybercriminals AI doesn’t just write better—it automates at scale, asks that used to take attackers days (researching targets, drafting emails, adjusting tone) now take minutes.
🎯 Hyper-Personalization at Scale AI scrapes LinkedIn, GitHub, press releases—even vacation posts—to craft messages that reference your projects, your deadlines. They don’t look like scams—they feel like business as usual.
🗣️ Deepfakes Are Real (New Oxymoron) 30 seconds of audio is enough to clone your voice. Add video synthesis, and attackers can put your CFO in a Zoom room they never joined.
⚡ Attacks at Machine Speed AI can generate thousands of unique phishing campaigns in minutes, in multiple languages, across every channel. Detection tools built for static “campaigns” are overwhelmed.
💬 AI-Driven Chatbots Scammers deploy AI “agents” that hold believable customer-service conversations, quietly extracting sensitive data while sounding perfectly human.
🌍 Real-Time Language Switching Attackers can move seamlessly between languages, making global operations fair game.
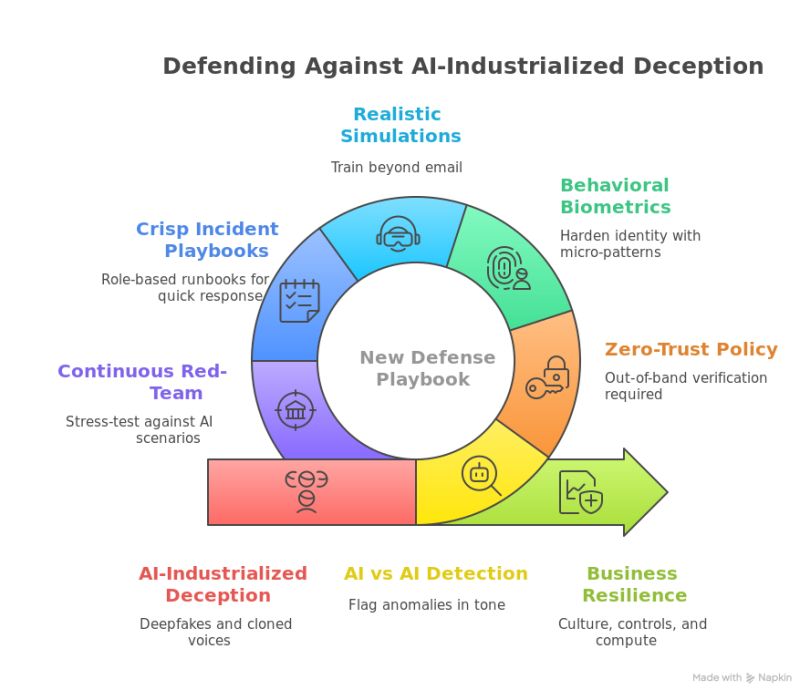
🛡️ The New Defense Playbook
🔍 AI vs AI Rely on ML-driven anomaly detection—tone shifts, timing mismatches, login irregularities—not gut instinct.
🔐 Zero-Trust in Practice Every sensitive request (fund transfers, account changes, vendor onboarding) must be verified out-of-band channels. No exceptions.
🧬 Behavioral Biometrics Typing cadence, mouse movements, and vocal rhythm provide identity signals are harder to fake.
🎭 Realistic Simulations Don’t just run phishing emails. Train staff with deepfake video calls, AI voice scams, and live chat manipulations.
📑 Incident Playbooks Seconds matter when AI is moving faster than policy. Equip teams with clear, role-based runbooks that remove hesitation.
⚡ Audit Now Red-team your defenses against AI scenarios. If you haven’t tested for deepfakes or hyper-personalized lures, you don’t know your exposure.
💡 Bottom line:
Social Engineering 2.0 is not an “IT problem.” It’s a business resilience challenge. The organizations that win will blend zero-trust discipline, AI-driven defense, behavioral verification, and cultural vigilance.
Reference:
#CyberSecurity #AI #ZeroTrust #RiskManagement #BoardStrategy #Deepfakes #Phishing #WomenInTech #WomenWhoCode #WISE